Cutting out the middle man.
When passing credit card numbers or passwords to a website, we're told to look for the padlock in the corner of your browser window.
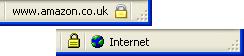
The padlock icon tells you two things.
A - The link between your computer and the web server is private.
B - The link is with the real server.
Setting up a private link is very simple, now all the mathematics have been sorted out. The problem comes with the "Man in the middle" scenario.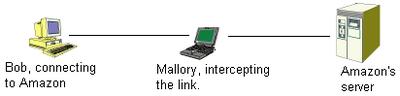
Mallory is the bad guy, pretending to be Amazon. Bob thinks that he has a secure link to the real Amazon, but instead he has a secure link to Mallory.
This form of attack doesn't necessarily involve cutting and patching wires. Possibly the most common form of man-in-the-middle is known as "Phishing".
Here, the attacker sets up a fake website with a similar name to a well known website, usually a bank. He then sends a mass of spam posing as the real company, asking customers to click on a link in the email, leading to the fake site. In so attempting to trick people into revealing their personal details and credit card number.
Phishing attacks are easy to launch, but easy to defeat. The real site is unaffected by the existence of the phishing site, so typing in the site address or using a known bookmark will defeat this specific form of attack.
The solution for all forms of man-in-the-middle attack is the Certificate Authority, which are often collectively abbreviated to just CA. (Not to be confused with Canada, California, Carlisle, Calcium or Computer Associates.)
To see them at work, click on the padlock icon. Here's what Firefox says. (IE does something similar.)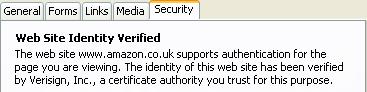
Verisign is the biggest of the CA companies. When someone wants to build a secure website, like Amazon, they go to a CA who will check them out. If the website meets the CA's criteria, they will issue a certificate which our browsers can read and verify. (Using lots more clever mathematics.)
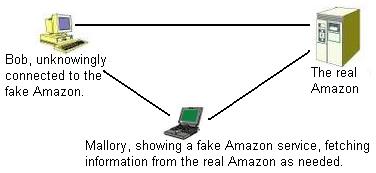
That certificate stops Mallory's scheme from working. Your browser would look for a certificate issued by a trusted CA and warn you if it can't find one. Mallory would have to go to a CA and ask for a certificate for his fake Amazon. A good CA would refuse, but a bad CA would issue a certificate to anyone who pays enough.
There's nothing forcing a CA to be good, except the possibility that no-one will trust them anymore. So its essential that you only trust the trustworthy.
The message behind the padlock says that I trust Verisign. Do I? No-one asked me. In fact, your browser probably comes loaded with a list of CAs who you trust by default and membership of this list is the gift of the browser makers.
For sure, you can edit the list, but browsers don't tend to make easy for you. Few people know the list exists, let alone how to edit it. Is this a problem? None of the trusted-by-default CAs have (yet) gone rouge. Can it last?
If the CA market were open to more choice by the public, a new CA could promote itself on the basis that they only issue certificates to genuine businesses, rejecting even phishing sites. People might add that CA to their trusted list, making a mental note to look for this CA before typing in a credit card number.
If that new CA screwed up by giving a certificate to AMAZØN.com, people would not trust that CA again. Market forces in action.
A good step would be for the browsers to stop shipping their browsers with a list of trusted CAs. That way, all the CAs would have to justify their trustworthiness to the public rather than the fait accompli by the browser makers we have now. This would level the playing field for new CA companies.
With this, the public would be expected to manage the trust list themselves, so the user interface will need to be improved to allow it. (I have several designs in my notebook if the browser makers want to hire me.)
Nice plan, but it will never happen. Imagine if Firefox did this, and an IE user decided to try out Firefox. It would all work very well for a few days, until he tries to buy something from Amazon, logging into the secure server.
"It worked just fine with IE!" he'll say. "This Firefox is going on about certificates, and I just want to get into my Amazon account."
Editing the trusted list in our browsers hasn't been made easy for us and the CA companies are not well known. Most of us don't have the time or inclination to do the research. So, until a better way comes along, I suggest we look for the padlock and don't follow links in emails.

The padlock icon tells you two things.
A - The link between your computer and the web server is private.
B - The link is with the real server.
Man in the middle
Setting up a private link is very simple, now all the mathematics have been sorted out. The problem comes with the "Man in the middle" scenario.

Mallory is the bad guy, pretending to be Amazon. Bob thinks that he has a secure link to the real Amazon, but instead he has a secure link to Mallory.
This form of attack doesn't necessarily involve cutting and patching wires. Possibly the most common form of man-in-the-middle is known as "Phishing".
Here, the attacker sets up a fake website with a similar name to a well known website, usually a bank. He then sends a mass of spam posing as the real company, asking customers to click on a link in the email, leading to the fake site. In so attempting to trick people into revealing their personal details and credit card number.
Phishing attacks are easy to launch, but easy to defeat. The real site is unaffected by the existence of the phishing site, so typing in the site address or using a known bookmark will defeat this specific form of attack.

Certificate Authority
The solution for all forms of man-in-the-middle attack is the Certificate Authority, which are often collectively abbreviated to just CA. (Not to be confused with Canada, California, Carlisle, Calcium or Computer Associates.)
To see them at work, click on the padlock icon. Here's what Firefox says. (IE does something similar.)

Verisign is the biggest of the CA companies. When someone wants to build a secure website, like Amazon, they go to a CA who will check them out. If the website meets the CA's criteria, they will issue a certificate which our browsers can read and verify. (Using lots more clever mathematics.)
That certificate stops Mallory's scheme from working. Your browser would look for a certificate issued by a trusted CA and warn you if it can't find one. Mallory would have to go to a CA and ask for a certificate for his fake Amazon. A good CA would refuse, but a bad CA would issue a certificate to anyone who pays enough.
There's nothing forcing a CA to be good, except the possibility that no-one will trust them anymore. So its essential that you only trust the trustworthy.
(Not) Fixing it
The message behind the padlock says that I trust Verisign. Do I? No-one asked me. In fact, your browser probably comes loaded with a list of CAs who you trust by default and membership of this list is the gift of the browser makers.
For sure, you can edit the list, but browsers don't tend to make easy for you. Few people know the list exists, let alone how to edit it. Is this a problem? None of the trusted-by-default CAs have (yet) gone rouge. Can it last?
If the CA market were open to more choice by the public, a new CA could promote itself on the basis that they only issue certificates to genuine businesses, rejecting even phishing sites. People might add that CA to their trusted list, making a mental note to look for this CA before typing in a credit card number.
If that new CA screwed up by giving a certificate to AMAZØN.com, people would not trust that CA again. Market forces in action.
Fixing it
A good step would be for the browsers to stop shipping their browsers with a list of trusted CAs. That way, all the CAs would have to justify their trustworthiness to the public rather than the fait accompli by the browser makers we have now. This would level the playing field for new CA companies.
With this, the public would be expected to manage the trust list themselves, so the user interface will need to be improved to allow it. (I have several designs in my notebook if the browser makers want to hire me.)
Nice plan, but it will never happen. Imagine if Firefox did this, and an IE user decided to try out Firefox. It would all work very well for a few days, until he tries to buy something from Amazon, logging into the secure server.
"It worked just fine with IE!" he'll say. "This Firefox is going on about certificates, and I just want to get into my Amazon account."
Epilogue
Editing the trusted list in our browsers hasn't been made easy for us and the CA companies are not well known. Most of us don't have the time or inclination to do the research. So, until a better way comes along, I suggest we look for the padlock and don't follow links in emails.




1 Comments:
Very interesting and informative
By Anonymous, At
5:11 AM, October 25, 2005
Anonymous, At
5:11 AM, October 25, 2005